Introduction
The BMENUA0100 module can be configured to operate in either Secured or Standard mode. The 3-position rotary selector switch on the back of the module determines the operating mode.
The three rotary switch positions are:
Secured mode
Standard mode
Security Reset
The module’s default, out-of-the-box configuration, is the Secured mode.
You can view the current position of the rotary switch in the Home page of the module web pages.
Because the rotary selector switch is not accessible while the module is on the rack, the switch position can be changed only when the module is powered off and removed from the rack. After a new switch position is selected, the module can be re-inserted into the rack and power applied.
Changing Operating Mode
Each time you switch the cybersecurity operating mode from Secured mode to Standard mode, or from Standard mode to Secured mode, perform a Security Reset operation before configuring the new mode.
The position of the rotary switch determines the operating state of the module, as follows:
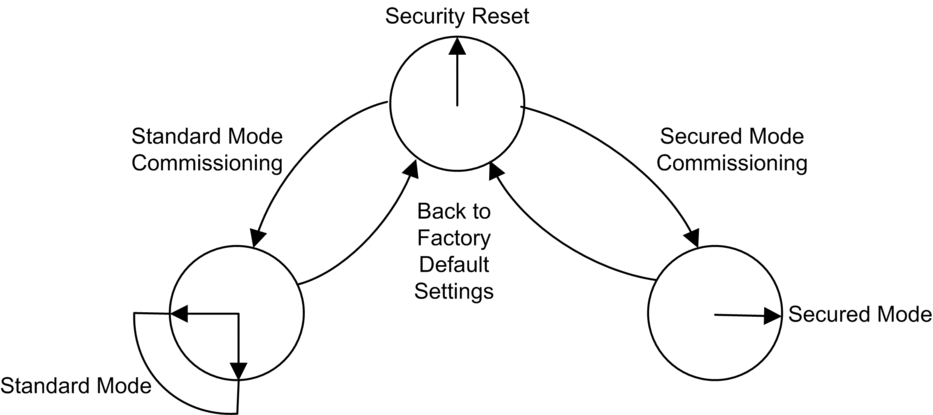
A new (out-of-the-box factory default) module, or a module for which a Security Reset has been performed, can be commissioned for either Standard mode or Secured mode operations.
The process for configuring the module for Secured mode operations varies, depending on whether you are connecting to the module configuration settings for the first time after performing a security reset:
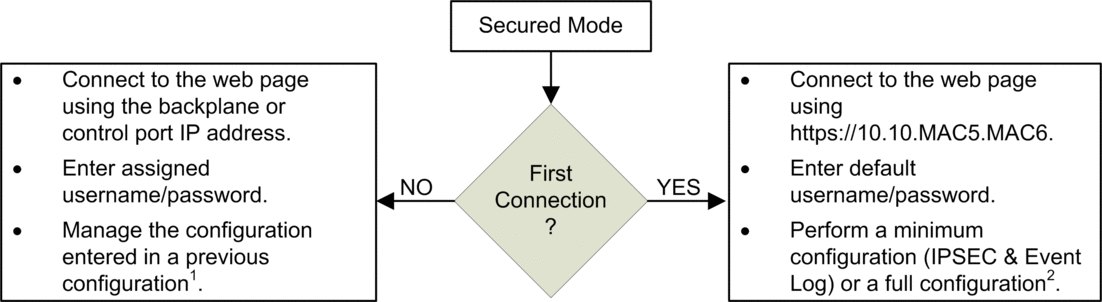
1 For information about managing the configuration, refer to the configuration chapter.
2 For information on performing a configuration on first connection, refer to the topic Secured Mode Commissioning.
Secured Mode
When operating in Secured mode, the module will not engage in process communications – over either the control port or the backplane port – until valid cybersecurity settings have been configured. After Secured mode has been configured, you can configure cybersecurity settings using the module web pages, which can be accessed via the HTTPS protocol over either the backplane or control ports. In Secured mode, the module supports the level of cybersecurity that is specified in the cybersecurity configuration. Only after cybersecurity settings have been configured, can IP address, NTP client, and SNMP agent settings be configured using the Control Expert configuration software.
Standard Mode
When operating in Standard mode, module communications can begin immediately. Cybersecurity settings are not required and cannot be configured. Only the IP address and other settings available in Control Expert can be configured.
Security Reset
The Security Reset command restores the out-of-the-box factory default configuration settings. It deletes any existing cybersecurity configuration, white lists, certificates, and role based access control settings. While the process of restoring factory default settings is ongoing, the RUN LED continues blinking green. After completion of process, the RUN LED turns to solid green, and all services are disabled. To complete the security reset, either cycle power (off, then on) to the BMENUA0100 module, or physically remove the module from the rack (which turns off power) then re-insert the module into the rack (which turns power back on).
This setting can be made using either the rotary switch or the web pages (when operating in Secured mode):
If set via rotary switch: the module ceases to be functional until the module is removed from the rack, the rotary switch is re-set to either the Secured or Standard position, and the module is again placed on the rack. The necessary configuration(s) will need to be applied.
If set via the web pages: upon completion of the process cycle power (off / on) to – or hot swap – the module in Standard or in Secured mode. Both the cybersecurity and IP address settings need to be configured.
No device certificates are preserved.
All services are disabled except for HTTPS, which is used to create the cybersecurity configuration via the control port.
Factory default settings are applied, including:
Username / Password default settings.
IP address default setting of 10.10.MAC5.MAC6.
Default Username / Password Combination
The default username / password combination depends on the cybersecurity operating mode setting:
Secured mode: admin / password
Standard mode: installer / Inst@ller1
Functions Supported by Secured and Standard Operating Modes
The following functions are supported by the BMENUA0100 module in Secured and Standard modes:
Security Mode |
Standard mode |
Secured mode |
|||||
|---|---|---|---|---|---|---|---|
Control port |
Disable |
Enable |
Disable |
Enable |
|||
Ethernet port |
Backplane |
Backplane |
Control port |
Backplane |
Backplane |
Control port |
|
OPC UA Comm |
Yes |
No |
Yes |
Yes |
No |
Yes |
|
Security Settings (4) |
None |
– |
None |
None, Sign, Sign&Encrypt (default value) |
– |
None, Sign, Sign&Encrypt (default value) |
|
User authentication |
No authentication (anonymous) |
– |
No authentication (anonymous) |
Operator, Engineer, No authentication (anonymous) |
– |
Operator, Engineer, No authentication (anonymous) |
|
SNMP V1 |
Yes (1, 2) |
Yes (1, 2) |
Yes (1, 2) |
Yes (1) |
Yes (1) |
Yes (1) |
|
SNMP V3 |
Yes (1, 2) |
Yes (1, 2) |
Yes (1, 2) |
Yes (1) |
Yes (1) |
Yes (1) |
|
NTP V4 |
Client only (1) |
Client (1), Server |
Yes, Client only (1) |
Client only (1) |
Client (1), Server |
Yes, Client only (1) |
|
Event Log |
No |
No |
No |
Yes |
Yes |
Yes |
|
IPSec |
No |
No |
No |
No |
No |
Yes for Modbus, SNMP V1/V3, NTP V4 (3) and Syslog (IPSec enabled by default) |
|
Web CS Config change (HTTPS) |
No |
No |
No |
Yes |
Yes |
Yes |
|
User authentication |
– |
– |
– |
Admin |
Admin |
Admin |
|
Network Services Comm server Enable/Disable |
If supported, always enabled (refer above) |
If supported, always enabled (refer above) |
If supported, always enabled (refer above) |
All services are configurable (disabled by default) |
All services are configurable (disabled by default) |
All services are configurable (disabled by default) |
|
Web Diagnostic (Home and Diagnostic pages only) |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
User authentication |
Installer (default credentials) |
Installer (default credentials) |
Installer (default credentials) |
Admin, Operator, Engineer, Installer |
Admin, Operator, Engineer, Installer |
Admin, Operator, Engineer, Installer |
|
Firmware upgrade (HTTPS) |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes, if HTTPS enabled |
|
User authentication |
Installer (default credentials) |
Installer (default credentials) |
Installer (default credentials) |
Installer |
Installer |
Installer |
|
Filtering: Forward All |
– |
– |
(always enabled) |
– |
– |
Forward all protocols |
|
Filtering: Configured Forward Protocol |
– |
– |
– |
– |
– |
Forward of configured protocols |
|
Filtering: Control Expert Data Flows to Device Network (including CPU) (FTP, EIP, Explicit, Modbus, Ping) via IPv4 only5 |
– |
– |
Forward of Control Expert data flows from Control Network to Device Network (always enabled) |
– |
– |
Forward of Control Expert data flows from Control Network to Device Network (disabled by default) |
|
|
|||||||


