CSPN Introduction
CSPN (Certification de SÚcuritÚ de Premier Niveau) is a cyber security certification currently used in the country of France. A product with CSPN certification is expected to withstand a cyber attack driven by two man months of skilled hackers.The Modicon M580 platform is CSPN-certified. This topic describes the environment, programmable automation controller (PAC) configurations, and parameters that meet CSPN requirements to effect the highest level of security.
M580 Introduction
The M580 PAC is designed to control and command an industrial process continuously without human intervention. At each step, the PAC processes the data received from its inputs, the sensors, and sends commands to its outputs, the actuators. Exchanges with the supervision (HMI, SCADA) are performed via a BMENOC0301/0311 Ethernet communication module on the local rack with the PAC.The PAC can run in a hostile environment despite humidity, dust, or unusual temperatures for IT systems and strong EMC or mechanical constraints.
The following illustration describes a typical M580 platform architecture that can be vulnerable to a security attack:
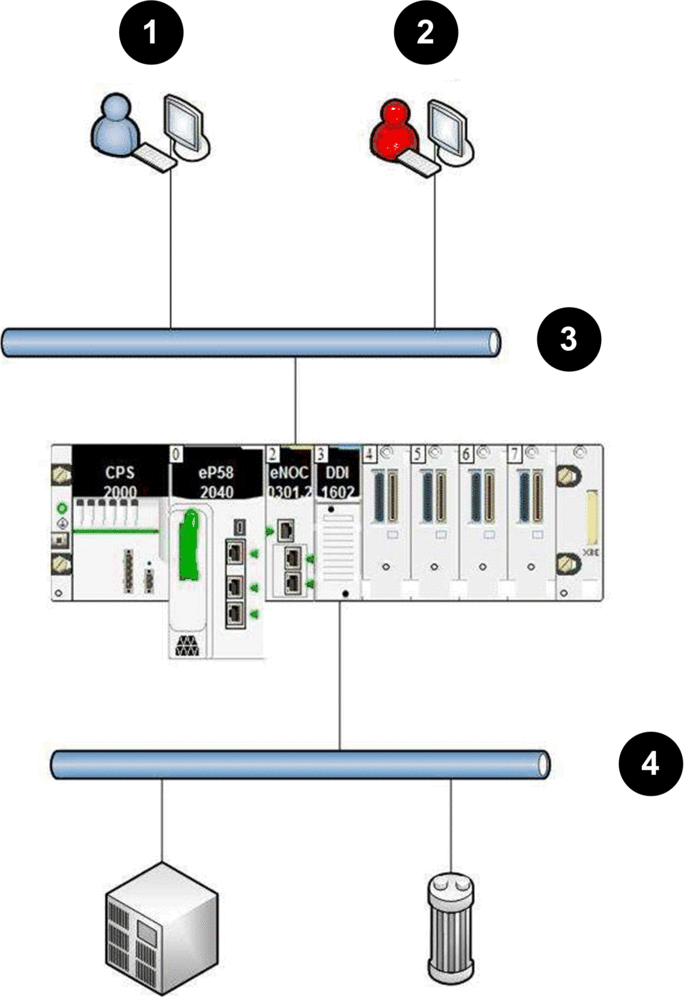
1 operator using Control Expert
2 attacker
3 supervision network
4 field network with no attacker
M580 Features
The M580 PAC offers the following features:
Feature |
Description |
|---|---|
user program execution |
An M580 PAC runs a user program that processes the inputs and updates the outputs. |
input/output management |
An M580 PAC can read local inputs and write local outputs. These inputs/outputs can be digital or analog and allow the M580 PAC to control and command the industrial process. |
communication with the supervision |
An M580 PAC can communicate with SCADA to receive commands and transmit process data using the Modbus protocol. |
administrative functions |
An M580 PAC includes administrative functions, which are provided in Control Expert , for configuration and programming. |
remote logging |
An M580 PAC supports the definition of a remote logging policy; it can log security and administrative events. |
M580 Configuration
A CSPN-certified M580 configuration includes these components:
Module |
Firmware |
Description |
|---|---|---|
BMEP58•0•0 |
V2.20 or later |
This CPU follows the security rules described in the security documents (see assumptions). |
BMENOC0301/0311 |
V2.11 or later |
This Ethernet module manages the encrypted communications with the upper layer (supervision and engineering software Control Expert ). |
User Profiles
Users that interact with the PAC for an improved implementation have the following predefined Control Expert Security Editor’s profiles:
User Profile |
Description |
|---|---|
ReadOnly |
No application modification is authorized. |
Operate |
Only application execution and parameter modification are enabled. |
Program |
All functions are enabled. |
Improved Implementation
These items contribute to a healthy environment for an improved implementation:
Item |
Security Considerations |
|---|---|
security documentation |
All recommendations in the documentation (user guides, white papers, etc) are applied prior to the evaluation. |
administrators |
System administrators are competent, trained, and trustworthy. |
premises |
Access to the PAC location is restricted to trustworthy people. In particular, an attacker does not have access to the physical ports of the PACs. Since identical products can be purchased freely, the attacker can obtain one to research vulnerabilities by any possible means. |
unevaluated services disabled |
Any services that are not covered by the security target are disabled in the configuration or by a user program (as described in the security documentation). |
user application verification |
The integrity of the Control Expert application is controlled by the administrator before it is loaded in the PAC. |
active logging |
The logging function is operational and the logs are not corrupt. |
log checking |
System administrators regularly check the local and remote logs. |
first configuration |
The initial configuration is uploaded to the PAC through the USB interface, and the PAC is unplugged from the network. |
firmware upgrade |
The firmware upgrade is performed through the USB interface, and the PAC is unplugged from the network. |
strong passwords |
System administrators employ strong passwords that combine uppercase letters, lowercase letters, numbers, and special characters. |
Operating Modes
The following operating modes are compliant with CSPN requirements:
During commissioning phase, initial configuration of the PAC can be done with either a Control Expert engineering station connected in point-to-point to the Ethernet port or to the local USB port of the PAC.
In normal operating conditions (running mode, SCADA connected on the Ethernet control network), confirm that Control Expert is disconnected.
Perform any further modification of the configuration or application program with Control Expert connected to the USB port of the PAC.
Cyber Security Parameters
This table describes the cyber security parameters:
Parameter |
Topic |
User Guide |
|---|---|---|
ACL activated. |
Configuring Security Services |
Modicon M580 BMENOC0301/0311 Ethernet Communications Module User Guide |
IPsec activated on BMENOC0301/0311 with maximum security. |
Configuring Security Services |
|
Enforce security selected (FTP, TFTP, HTTP, DHCP/BOOTP, SNMP, EIP, NTP protocols deactivated). |
Configuring Security Services |
|
Log activated. |
Logging DTM and Module Events to the Syslog Server |
|
RUN/STOP by input only activated. |
Managing Run/Stop Input |
Modicon M580 Hardware Reference Guide |
Memory protection activated. |
Memory Protect |
|
Helping secure a project:
|
Helping Secure a Project in Control Expert |
|
No upload information stored inside CPU. |
PAC Embedded Data |
EcoStruxure™ Control Expert, Operating Modes |
Default password for FTP service changed. |
Firmware Protection |
|
Application sections are set with no read/write access. |
Section and Subroutine Protection |
Critical Assets
Environment: This table shows the assets that are critical to the environment:
Asset |
Description for Proper Use |
|---|---|
control-command of the industrial process |
The PAC controls and commands an industrial process by reading inputs and sending commands to actuators. The availability of these actions is protected. |
engineering workstation flows |
The flows between the PAC and the engineering workstation are protected in integrity, confidentiality, and authenticity. |
Security requirements for the environmental critical assets:
Asset |
Availability |
Confidentiality |
Integrity |
Authenticity |
|---|---|---|---|---|
control-command of the industrial process |
X |
|||
engineering workstation flows |
X |
X |
X |
PAC: This table shows the assets that are critical to the PACs:
Asset |
Description for Proper Use |
|---|---|
firmware |
The firmware is protected both in integrity and authenticity. |
PAC memory |
The PAC memory contains the PAC configuration and a program that is loaded by the user. Its integrity and authenticity are protected while it is running. |
execution mode |
The integrity and authenticity of the execution mode of the PAC are protected. |
user secrets |
All passwords that are used to perform authentication are held in the confidence by the appropriate users. |
Security requirements for the PAC critical assets:
Asset |
Availability |
Confidentiality |
Integrity |
Authenticity |
|---|---|---|---|---|
firmware |
X |
X |
||
PAC memory |
X |
X |
||
execution mode |
X |
X |
||
user secrets |
X |
X |
Security Threats
Threats considered by attackers controlling a device plugged into the supervision network:
Control-Command of the Industrial Process |
Engineering Workstation Flows |
Firmware |
PAC Memory |
Execution Mode |
User Secrets |
|
|---|---|---|---|---|---|---|
denial of service |
Av |
|||||
firmware alteration |
I, Au |
|||||
execution mode alteration |
, AuI |
|||||
memory program alteration |
I, Au |
|||||
flows alteration |
Av |
Au, C, I |
C, I |
|||
Av: availability I: integrity C: confidentiality Au: authenticity |
||||||
Type of Threat |
Description |
|---|---|
denial of service |
The attacker manages to generate a denial of service on the PAC by performing an unexpected action or by exploring a vulnerability (sending a malformed request, using a corrupted configuration file...). This denial of service affect the entire PAC or only some of its functions. |
firmware alteration |
The attacker manages to inject and run a corrupted firmware on the PAC. The code injection may be temporary or permanent, and does not include any unexpected or unauthorized code execution. A user may attempt to install that update on the PAC by legitimate means. Finally, the attacker manages to modify the version of the firmware installed on the PAC without having the privilege to do so. |
execution mode alteration |
The attacker manages to modify the execution mode of the PAC without being authorized (a stop command for instance). |
memory alteration |
The attacker manages to modify, temporarily or permanently, the user program or configuration that run in the PAC memory. |
flows alteration |
The attacker manages to corrupt exchanges between the PAC and an external component without being detected. He can perform attacks such as credential theft, access control violation, or control-command of the industrial process mitigation. |
Persistent Denial of Service |
Firmware Alteration |
Execution Mode Alteration |
Memory Alteration |
Flows Alteration |
|
|---|---|---|---|---|---|
malformed input management |
X |
||||
storage of secrets |
X |
||||
athentication on administrative interface |
X |
||||
access control policy |
X |
||||
firmware signature |
X |
||||
integrity and authenticity of PAC memory |
X |
||||
integrity of the PAC execution mode |
X |
||||
more secure communication |
X |
Type of Threat |
Description |
|---|---|
malformed input management |
The PAC has been developed to correctly handle malformed input, particularly malformed network traffic. |
strength of secrets |
The PAC has been developed to correctly handle malformed input, particularly malformed network traffic.
|
authentication on administrative interface |
Session tokens are protected against hijack and replay; they have a short lifespan. The identity and permissions of the user account are systematically checked before any privileged action.An application password is set in each configuration, which helps prevent any modification of the PAC from a non-authentic user. |
access control policy |
The access control policy helps guarantee the authenticity of privileged operations, i.e., operations that can alter identified critical assets.The access control list (ACL) is activated in each configuration, and only identified IP addresses can connect to the PAC. |
firmware signature |
At each firmware update, integrity and authenticity of the new firmware are checked before updating. |
integrity and authenticity of PAC memory |
The memory protection feature is activated in each configuration, which helps prevent the modification of the running program without an action in specific inputs or outputs. If no input/output module is installed, the programming interface is blocked.The PAC helps ensure the integrity and authenticity of the user program, so that only authorized users can modify the program. The memory protection also helps ensure the configuration protection, which includes several security parameters:
|
integrity of the PAC execution mode |
The PAC helps ensure that the execution mode can only be modified by authorized users that are authenticated.The RUN/STOP by input only feature is activated, which helps prevent the possibility of changing the RUN/STOP status through the Ethernet interface. |
encrypted communication |
The PAC supports encrypted communication, protected in integrity, confidentiality, and authenticity (IPsec encrypted with ESP).The FTP protocol is disabled, and IPsec helps secure Modbus communication through the BMENOC0301/0311 module. |


