Introduction
The goal of encrypted communication is to help protect the communication channels that allow remote access to the critical resources of the system (such as PAC embedded application, firmware). IPsec (Internet Protocol Security) is an open standard defined by the IETF to provide protected and private communications on IP networks provided by using a combination of cryptographic and protocol security mechanisms. Our IPsec protection implementation includes anti-replay, message integrity check, and message origin authentication.
IPsec is supported on Microsoft Windows versions 7 and 10. It is initiated from the PC operating system.
Description
The IPsec function helps to secure:
The control room Modbus access to the PAC CPU through the BMENOC0301/11 module.
The control room access to the communication services running inside the BMENOC0301/11 module in server mode (Modbus, EtherNet/IP, HTTP, FTP, SNMP).
Wireless connection: When a PMXNOW0300 wireless module is used to configure a wireless connection, configure this module with the maximum security settings available (WPA2-PSK).
Architecture Example
The purpose of the following figure is to illustrate through an example the various protocols or services involved in a encrypted communication from the control room to a Modicon M580 PAC.
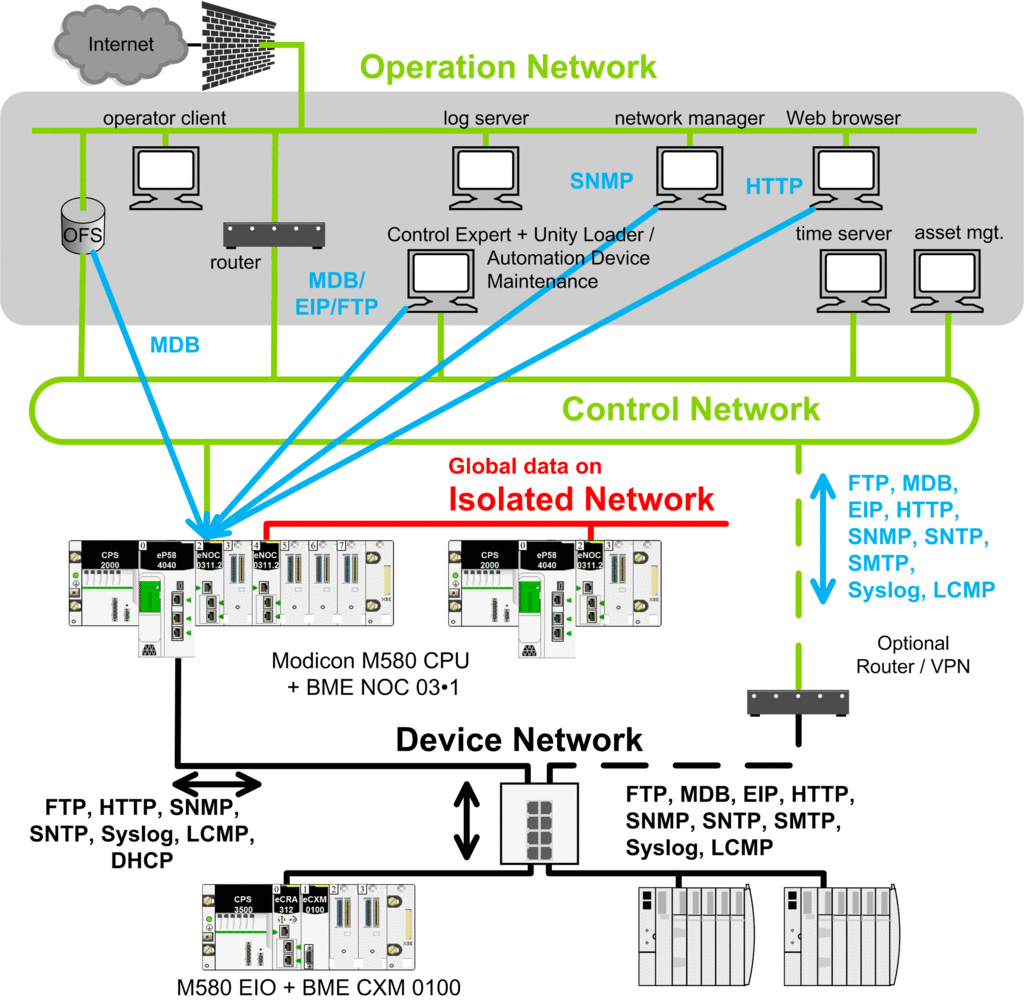
 Encrypted communication
(IPsec).
Encrypted communication
(IPsec).
 Non IPsec communication.
Non IPsec communication.
Data Flow with Encrypted Communication Capability
Use these services to facilitate communications when IPsec is enabled:
Ethernet Service |
Data Flows Security |
|---|---|
EIP class 3 server |
These services are supported through encrypted connections. |
FTP server, TFTP server |
|
HTTP |
|
ICMP (ping, etc.) |
|
Modbus server (port 502) |
|
ARP |
These services are supported through encrypted and unencrypted connections. NOTE: This traffic bypasses the IPsec protocol handling in the BMENOC and therefore
does not use IPsec.
|
LLDP |
|
loop check protocol |
|
Modbus scanner |
|
RSTP |
|
DHCP, BootP client |
These services are not supported when IPSec is enabled. NOTE: Before IKE/IPsec is initiated
by the peer (PC), this traffic is not secured by IPSec. After IKE/IPSec is established,
this traffic is encrypted by IPsec. Protocol
could be supported, but only if packet recipient is a PC with IPSec configured and enabled.
|
DHCP, BootP server |
|
EIP class 1, TCP (forward open) |
|
EIP class 1, UDP (data exchange) |
|
Modbus client |
|
NTP client |
|
SNMP agent |
|
SNMP traps |
|
Syslog client (UDP) |
IPsec is an OSI layer 3 protection. OSI layer 2 protocols (ARP, RSTP, LLDP, loop check protocol) are not protected by IPsec.
Global Data communication flow (using BMXNGD0100 modules) cannot be secured by IPsec. Use such a configuration on an isolated network.
Limitations
IPsec limitations in the architecture: BMENOC0301/11 does not support IP forwarding to device network.
If transparency is required between control and device network, an external router/vpn is needed to provide an encrypted communication between the control and device network (as shown in previous architecture example figure).
Transparency is required to perform the following operations from the control network:
Update Modicon M580 CPU firmware from the Automation Device Maintenance through HTTPS service or from Unity Loader software through FTP service.
Perform a network diagnostic of Modicon M580 CPU from a network management tool through SNMP service.
Diagnose a Modicon M580 CPU from a DTM through EIP service.
Diagnose a Modicon M580 CPU from a Web browser through HTTP service.
Log Modicon M580 CPU cyber security events in a syslog server through syslog service.
Synchronize Modicon M580 CPU time from a global time server through NTP service.
Setting Up IPsec Communication in the System Architecture
Proceed with the following steps to set up the IPsec communication:
In the control room, identify the client authorized applications that need to communicate with the PAC using Modbus (Control Expert, Automation Device Maintenance, Unity Loader, OFS, customer applications such as SGBackup, ...).
Configure IPsec on each PC supporting these authorized applications.
In the control room, identify the client authorized applications that need to communicate with each BMENOC0301/11 module configured in the local rack (Control Expert DTM, Automation Device Maintenance, Unity Loader, SNMP manager, Web browser, Web designer for FactoryCast BMENOC0301/11 module).
Configure IPsec on each PC supporting these authorized applications.
Incorporate a BMENOC0301/11 module with IPsec function on the backplane of each PAC connected to the control network.
To configure the IPsec function on a BMENOC0301/11 module, proceed in 2 steps:
Enable IPsec function.
Configure a pre-shared key. A pre-shared key is used to build a shared secret allowing two devices to authenticate each other.
NOTE: Because IPsec relies on this shared secret, it is a key element in the security policy that is managed by the security administrator only. To increase the security of the pre-shared key, we recommend that you use an external tool such as KeePass to generate an appropriate character string.
The BMENOC0301/11 module configuration is performed with Control Expert. The application is initially downloaded through USB link, future downloads are performed through Ethernet with an IPsec function if IPsec is enabled.
Each PC supporting IPsec needs to comply with the following requirements for IPsec configuration:
Use Microsoft Windows 10 OS.
Have the administrator rights to configure IPsec.
Once the IPsec configuration is performed, set the Windows account as a normal user account without administrator privilege.
Harden the PC as explained in the Hardening the PC topic.
More details on configuration are provided in the Configuring IP Secure Communications topic.
Generate Pre-Shared Keys with the Highest Security
The security of IPsec communications relies on the complexity of the pre-shared key. We recommend the use of specialized tools to generate pre-shared keys of the highest security.
One such tool is KeePass, which you can download as freeware from the Internet. Download and install KeePass to your PC and launch it.
Configure and use KeePass v2.34 to generate passwords that can be used as pre-shared keys:
Step |
Action |
|---|---|
1 |
Create a new key database folder (), |
2 |
In the dialog box, enter a folder name in the field and record your modifications. |
3 |
In the dialog box, enter a . Enter the password again in the password field. |
4 |
Press to open and press again. |
5 |
In the new database dialog box, expand . |
6 |
Select and add an entry (). |
7 |
In the field, enter a name for your module (for example, eNOC). |
8 |
In the field, enter a user name. |
9 |
Click the icon. |
10 |
Select . |
11 |
Press to populate the and fields. |
12 |
Open the dialog box (). |
13 |
Make these selections at :
NOTE: These characters are not accepted for use in
the pre-shared key:
|
14 |
Press . |
15 |
Right-click on your device in the list and scroll to . |
16 |
Open the security configuration screen in Control Expert. |
17 |
Paste the key in the IPsec configuration screen. |
Diagnose IPsec Communication in the System Architecture
Information on IPsec diagnostic in the system architecture is provided in the Configuring IP Secure Communications topic.


