Certificates Management and PKI
- Certificates Management without PKI: Use this certificate
management method if your system does not include a CA. Manage certificates
in the certificates management web pages as follows:
Self-signed only is the system default PKI mode.
You can only switch the device factory reset mode to self-signed only mode.
Manage the Certificate Trust List using the Add and Delete functions to create an allowed list that is authorized to communicate with the RTU module.
Click the Download button (below) to export the RTU module certificate to communicated devices.
Certificates Management with PKI: Access the PKI Configuration web page and configure the parameters as described below.
Access the Page
Access the PKI Configuration web page through the SETUP tab for the BMENOR2200H module ().
PKI Parameters
Manage the allotment and acceptance of certificates with the following PKI parameters if your system includes a CA.
Parameter |
Description |
|---|---|
PKI Mode |
Self-Signed only: This is the default PKI mode for the system. |
| CA only: All installed devices support PKI. Manually enroll each RTU module with the CA. |
|
Self-Signed & CA: Some installed devices do not support PKI. Considerations:
Manually enroll each RTU module with the CA. Manage the
trusted list to create an allowed list that is authorized to communicate
with the RTU module.
NOTE: Only certificates in the list
need to be managed.
|
|
Submit |
Click this button to assign the PKI mode. |
Parameter |
Description |
|---|---|
Subject |
This line identifies the host or party that controls the private key certification. |
Subject Alternative Name |
The structured name in this field includes the domain and sub-domain names and the IP addresses that the certificate secures. |
Issuer |
This field shows the entity that issued the certificate. |
Expiration Date |
This field shows the expiration date of the certificate. |
Download |
Click this button to export the RTU module certificate for HTTPS on your PC. |
Parameter |
Description |
|---|---|
1. Generate CSR |
Click this button to download on your PC a Certificate Signing Request (CSR) in the Privacy Enhanced Mail (.pem) format. |
2. Select the certificate file to upload |
Enter an X.509v3 certificate that is encoded in ASN.1 (DER). A CA installed in the device produced this
certificate from the downloaded CSR for the device.
NOTE: You can use
the Browse button to navigate to the file.
|
Upload |
Click this button to upload on the module an offline file that contains a configuration for communications with the CA by receiving the certificate through the CSR. |
NOTE: Refer
to the description of the manual
certificate-enrollment process.
|
|
PKI Mode Setting Flowchart
This diagram illustrates the user actions and events related
to changing the PKI mode setting: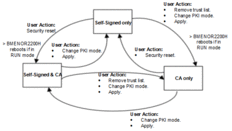
Execute Changes
Manual Enrollment
After configuring the RTU module in Control Expert, you can use the section to get a CSR file to be submitted to a CA. After submitting the CSR file, you can then extract the correspondent CA certificate. Thereafter, you can push this CA Certificate into the RTU module. The combined get and push operations manually enroll a certificate issued by a third-party CA. After the certificate is pushed, the server applies this certificate for the purpose of signing and encrypting its communication with the client.
The following is an overview of the manual certificate enrollment
process: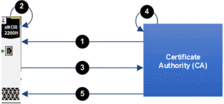
1 The BMENOR2200H imports a Root CA Management MENU from the certificate authority (CA).
2 The BMENOR2200H generates a certificate signing request (CSR).
3 The BMENOR2200H exports the CSR to the CA.
4 The CA executes the CSR and generates a certificate.
5 The BMENOR2200H imports the certificate from the CA.


