System Architecture
The following PlantStruxure architecture highlights the necessity to have a multi-layered architecture (with a control network and a device network) that can be more secured. A flat architecture (all equipment connected to the same network) cannot be secured properly.
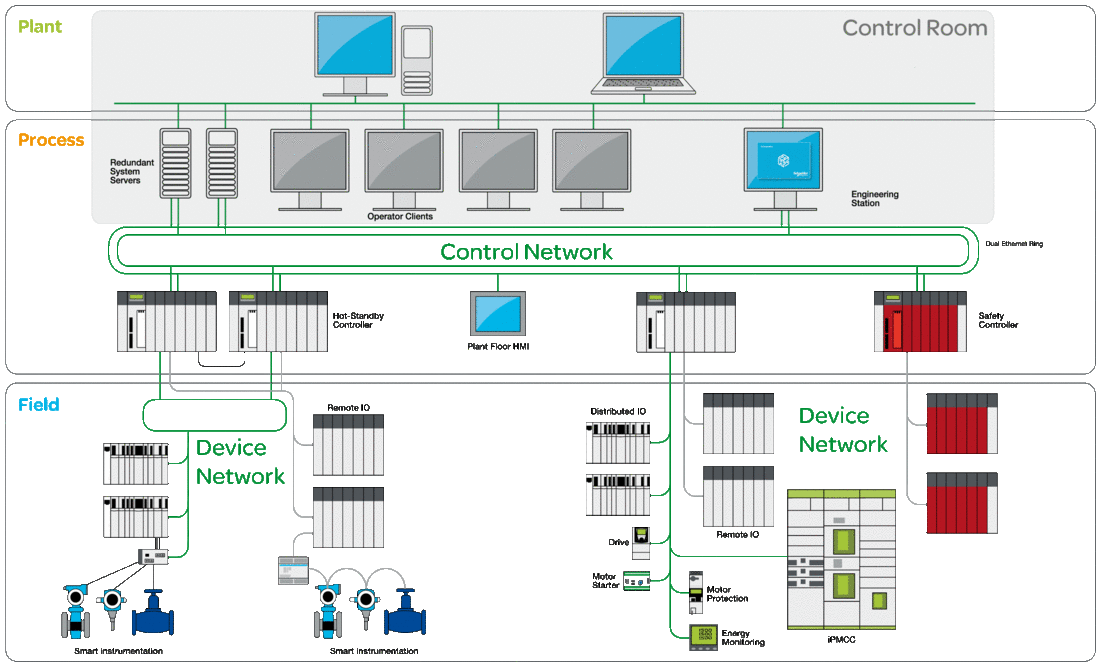
More Secured Communication
Equipment in the control room is more exposed to attacks than equipment connected to the device network. Therefore, implement more secured communication between the control room and the PAC and devices. Isolate the device network from the other network levels (such as control networks and remote networks).
In the system architecture above, the control room area is grayed to distinguish it from the PAC and devices.
More Secured Access to the USB Ports
The physical access to the CPU USB ports needs to be controlled.
More Secured Access to the Hot Standby Link and Device Network
Control the physical access to the Hot Standby link and to the device network.
Testing
Control Expert provides a simulator that you can use to test your application before commissioning it as part of your industrial automation system. The simulator conforms to the cyber security requirements that:
The simulator can be operated only with an application open in Control Expert.
The application open in the simulator cannot be uploaded from the simulator to the PLC.
For information on how to operate the simulator, refer to the help for the EcoStruxure™ Control Expert, PLC Simulator.


