Certificates Management With and Without PKI
The BMENUA0100 module relies upon certificates for authentication. To provide cybersecurity, each entity (including OPC UA clients and the OPC UA server embedded in the BMENUA0100) needs to manage a trust list of all certificates of devices/applications that communicate with it.
The method of certificate management depends on your system design, which may - or may not - apply a public key infrastructure (PKI) with a certificate authority (CA).
Certificate Management without PKI:
Use this certificate management method if your system does not include a CA. This management method is supported by BMENUA0100 modules with firmware v1.0 and higher. Manage certificates in the web pages as follows:
Set to .
Manage the using the and functions to create a whitelist for OPC UA clients that are authorized to communicate with the BMENUA0100 module.
Export the BMENUA0100 module certificate to OPC UA client devices using the command in the page.
Certificate Management with PKI:
Use this certificate management method if your system includes a CA. This management method is supported by BMENUA0100 modules with firmware v1.1 and higher. Manage certificates in the web pages as follows:
Set to either:
: if all installed OPC UA client devices support PKI.
: if some of the installed OPC UA client devices do not support PKI.
If is set to :
Manually enroll each BMENUA0100 module with the CA.
If is set to :
Manually enroll each BMENUA0100 module with the CA.
Manage the using the and functions to create a whitelist for OPC UA clients that are authorized to communicate with the BMENUA0100 module.
Updating the Certificate Trust List
After the first installation of BMENUA0100 firmware version 2.0 (BMENUA0100.2) or higher, you need to remove all user added certificates from the Certificate Trust List in the Certificates Management web page. You can do this by:
Manually removing these certificates using the Delete command, or
Setting the cybersecurity rotary switch to the Security Reset position.
After the Certificate Trust List is cleared, you can re-populate it with self-signed or CA issued certificates.
This task needs to be performed only on the first installation of firmware version 2.0 or higher. You do not need to repeat the procedure on subsequent installations of higher firmware versions.
Authentication Overview
An OPC UA client or a BMENUA0100 module can be authenticated in three ways:
For firmware version 1.0 and higher:
Self-signed certificate (only)
For firmware version 1.10 and higher:
PKI certificate issued by a third-party Certificate Authority (CA) only
PKI certificate issued by a CA and a self-signed certificate
To provide the required level of cybersecurity, each entity (OPC UA client, BMENUA0100) needs to manage a trust list of all certificates of devices/applications that communicate with it.
For firmware version 1.10 and higher, the BMENUA0100 module creates a self-signed certificate for:
Configuration of the cybersecurity settings via the module web pages
Diagnostic of the module via its web pages
Firmware upgrade
OPC UA application instance certificates to permit OPC UA clients to access the embedded OPC UA server in the BMENUA0100 module.
For firmware version 1.0 the module creates two certificates: one HTTPS certificate and one OPC UA certificate.
The expiration dates of the trusted certificates are made by reference to the internal Date and Time settings of the BMENUA0100 module. To avoid inconsistency, use the NTP service to update the Date and Time settings of the BMENUA0100 module, and check that the NTP server is accessible and has an updated Time and Date settings.
If you receive a BadCertificateHostnameInvalid error when attempting to connect your OPC UA client to the BMENUA0100 server in IPv6, it may be caused by a compressed IPv6 address (i.e., shortened IPv6 address). In this case check the IPv6 address that was used and, if necessary, replace it using an uncompressed format.
The BMENUA0100 module does not automatically manage the expiration dates of certificates. Instead, you need to manually manage certificate expiration dates.
Managing Certificates
In the BMENUA0100 module web pages, starting in the page, select to display links to the following application instance certificate management pages:
Refer to the topics Using GPOs/LGPOs and Applying MMC Group Policy Management for information regarding the Windows™ tools you can use to help manage certificates.
Certificate Extensions
To support communication with the BMENUA0100 module, self-signed and CA certificates need to include specific extensions, as follows:
Self-Signed Certificates:
KeyUsage (marked as critical):
DigitalSignature
KeyEncipherment (No usage for TLS suite based on ephemeral keys such as TLS_ECDHE_xxxx; usage for TLS_RSA_xxxx)
KeyCertSign: when the subject public key is used for verifying signatures on public key certificates (Value TRUE)
nonRepudiation (required by OPC UA standard)
dataEncipherment (required by OPC UA standard)
Subject Alt Name: In the SAN field the following values can be specified: IPAddress V4/V6, URI
Basic Constraints:
cA field: whether the certified public key may be used to verify certificate signatures (Value TRUE) and pathLenConstraint=0
Subject Key Identifier:
means of identifying certificates that contain a particular public 160-bit SHA-1 hash of the value of the BIT STRING subjectPublicKey (excluding the tag, length, and number of unused bits).
Extended Key Usage extension:
id-kp-serverAuth if TLS Web server authentication
id-kp-clientAuth if TLS Web client authentication
CA Certificates:
KeyUsage (marked as critical):
DigitalSignature
KeyEncipherment (No usage for TLS suite based on ephemeral keys such as TLS_ECDHE_xxxx; usage for TLS_RSA_xxxx)
KeyCertSign: when the subject public key is used for verifying signatures on public key certificates (value FALSE)
nonRepudiation (required by OPC UA standard)
dataEncipherment (required by OPC UA standard)
Subject Alt Name: In the SAN field the following values can be specified: IPAddress V4/V6, URI
Basic Constraints:
cA field: whether the certified public key may be used to verify certificate signatures (value FALSE)
Extended Key Usage extension:
id-kp-serverAuth if TLS Web server authentication
id-kp-clientAuth if TLS Web client authentication
CRL Distribution points
Authority Key Identifier:
Identification of the public key corresponding to the private key used to sign a certificate.
PKI Configuration
Use the page to specify the types of certificates accepted by the OPC UA server embedded in the module, including:
PKI Mode |
Description |
|---|---|
Self-Signed only |
Only certificates in the list (“white list”) need to be managed. |
CA only |
All system devices need certificates signed by a CA. |
Self-Signed and CA |
Certificates are managed as follows:
|
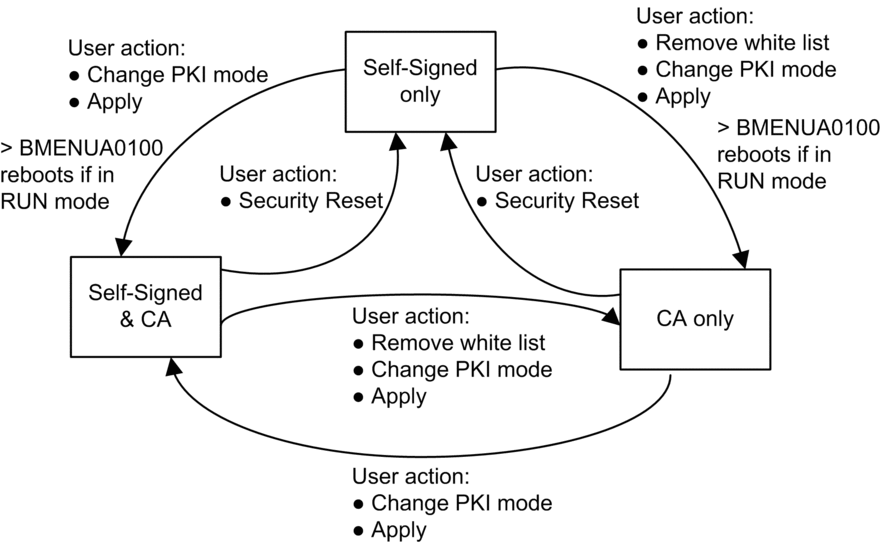
The following diagram illustrates the user actions and events related to changing the PKI mode setting:
Manual Enrollment
After configuring the BMENUA0100 module in Control Expert, you can use the page to "Get" a CSR file to be submitted to a CA. After submitting the CSR file, you can then extract the correspondent CA certificate. Thereafter, you can "Push" this CA Certificate into the BMENUA0100 module. The combined Get and Push operations manually enroll a certificate issued by a third-party CA. After the certificate is "pushed", the OPC UA server applies this certificate for the purpose of signing and encrypting its communication with the OPC UA client.
Confirm that the NTP client is enabled.
Check that the time setting for the BMENUA0100 module is the actual time.
The following is an overview of the manual certificate enrollment process:
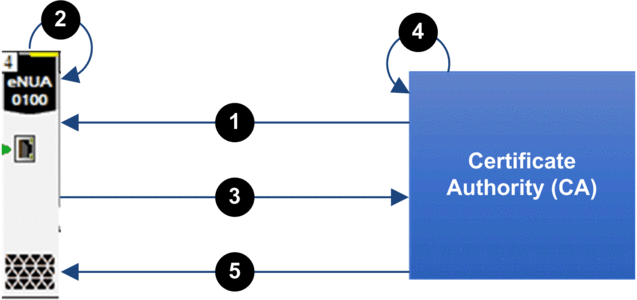
1 BMENUA0100 imports a CA certificate from the certificate authority (CA)
2 BMENUA0100 generates a certificate signing request (CSR)
3 BMENUA0100 exports the CSR to the CA
4 The CA executes the CSR and generates a certificate
5 BMENUA0100 imports the certificate from the CA
Refer to the Schneider Electric video “How to work with PKI mode “Self-Signed & CA” on BMENUA0100 module?” at https://www.se.com/us/en/faqs/FAQ000191153/.
Client Trust List Management
Only OPC UA clients that have provided the BMENUA0100 module with an application instance certificate can communicate with the OPC UA server embedded in the module. The module implements local (module-based) management of OPC UA application instance certificates, which are stored in a trust list. Use the commands on the web pages to , , or a certificate.
To add a certificate to the list:
Step |
Action |
|---|---|
1 |
In the trust list management menu, click . |
2 |
Click , then navigate to and select the certificate you want to add to the list. |
3 |
Click to add the certificate. |
4 |
Click to save the change to the configuration. |
To remove a certificate from the list:
Step |
Action |
|---|---|
1 |
In the trust list, click the certificate you want to remove |
2 |
Select . |
3 |
Click to remove the certificate from the list. |
4 |
Click to save the change to the configuration. |
Device Certificates Export
You can export the BMENUA0100 module certificate for both HTTPS and OPC UA in the page by clicking on the button
CA Certificates
The CA certificate is a public key certificate that identifies the certificate authority (CA) in a public key infrastructure (PKI). Use the page to push the CA certificate(s) in the device.
To add a certificate from the CA to the CA Certificates list:
Step |
Action |
|---|---|
1 |
Open the web pages for the module, and in the dialog, enter:
Click . |
2 |
Navigate to to access the certificates management tab, then select . |
3 |
In the list, click to add the CA certificate to the list. |
4 |
Apply the changes to the cybersecurity configuration. |


